May062020
DVWA-4.4 File Inclusion(文件包含)-Impossible-白名单
Impossible Level
查看源码
<?php
// The page we wish to display
$file = $_GET[ 'page' ];
// Only allow include.php or file{1..3}.php
if( $file != "include.php" && $file != "file1.php" && $file != "file2.php" && $file != "file3.php" ) {
// This isn't the page we want!
echo "ERROR: File not found!";
exit;
}
?>
可以...阅读全文
抢沙发
May062020
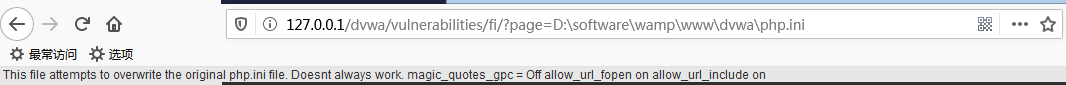
DVWA-4.3 File Inclusion(文件包含)-High-利用file协议绕过防护策略
High Level
查看源码
<?php
// The page we wish to display
$file = $_GET[ 'page' ];
// Input validation
if( !fnmatch( "file*", $file ) && $file != "include.php" ) {
// This isn't the page we want!
echo "ERROR: File not found!";
exit;
}
?>
fnmatch() 函数根据指定的模式来匹配文件名或字符串。
可以看到,High级别的代码使用了fnmatch函数...阅读全文
May062020
DVWA-4.2 File Inclusion(文件包含)-Medium-双写绕过str_replace替换规则
Medium Level
服务器端核心代码
<?php
// The page we wish to display
$file = $_GET[ 'page' ];
// Input validation
$file = str_replace( array( "http://", "https://" ), "", $file );
$file = str_replace( array( "../", "..\"" ), "", $file );//个人感觉这里的源码错了,应该改为"..\\",其中第一个反斜杠用来转义第二个反斜杠
?>
可以看到,Medium级别的代码增加了s...阅读全文
May062020
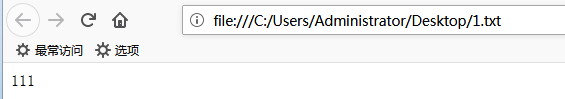
DVWA-4.1 File Inclusion(文件包含)-Low
File Inclusion
File Inclusion,意思是文件包含(漏洞),是指当服务器开启allow_url_include选项时,就可以通过php的某些特性函数(include(),require()和include_once(),require_once())利用url去动态包含文件,此时如果没有对文件来源进行严格审查,就会导致任意文件读取或者任意命令执行。文件包含漏洞分为本地文件包含漏洞与远程文件包含漏洞,远程文件包含漏洞是因为开启了php...阅读全文
May062020
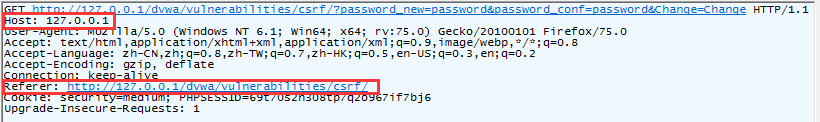
DVWA-3.4 CSRF(跨站请求伪造)-Impossible
Impossible Level
查看源码
<?php
if( isset( $_GET[ 'Change' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
$pass_curr = $_GET[ 'password_current' ];
$pass_new = $_GET[ 'password_new' ];
$pass_conf = $_GET[ 'password_conf' ];
// Sanitise curren...阅读全文
May062020
DVWA-3.3 CSRF(跨站请求伪造)-High-绕过token
High Level
查看源码
<?php
if( isset( $_GET[ 'Change' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
$pass_new = $_GET[ 'password_new' ];
$pass_conf = $_GET[ 'password_conf' ];
// Do the passwords match?
if( $pass_new == $pass_conf ) {
...阅读全文
May062020
DVWA-3.2 CSRF(跨站请求伪造)-Medium-绕过Referer验证
Medium Level
查看源码
<?php
if( isset( $_GET[ 'Change' ] ) ) {
// Checks to see where the request came from
if( stripos( $_SERVER[ 'HTTP_REFERER' ] ,$_SERVER[ 'SERVER_NAME' ]) !== false ) {
// Get input
$pass_new = $_GET[ 'password_new' ];
$pass_conf = $_GET[ 'password_conf' ];
// Do the passwords match?
...阅读全文
May062020
DVWA-3.1 CSRF(跨站请求伪造)-Low
Low Level
查看源码
<?php
if( isset( $_GET[ 'Change' ] ) ) {
// Get input
$pass_new = $_GET[ 'password_new' ];
$pass_conf = $_GET[ 'password_conf' ];
// Do the passwords match?---校验新密码和确认密码是否相同
if( $pass_new == $pass_conf ) {
// They do!---若相同,先使用mysqli_real_escape_string函数转义用户输入的新密码中的特殊字...阅读全文
May062020
DVWA-2.4 Command Injection(命令注入)-Impossible-安全的白名单
Impossible Level
查看源码
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
$target = $_REQUEST[ 'ip' ];
$target = stripslashes( $target ); //stripslashes()删除反斜杠
// Split the IP into 4 octects
$octet = e...阅读全文
May062020
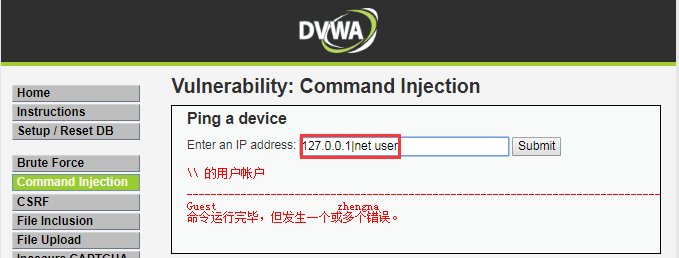
DVWA-2.3 Command Injection(命令注入)-High-绕过强的黑名单
High Level
查看源码
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$target = trim($_REQUEST[ 'ip' ]);
// Set blacklist
$substitutions = array(
'&' => '',
';' => '',
'| ' => '',
'-' => '',
'$' => '',
'(' => '',
')' => '',
'`' => '',...阅读全文