May062020
DVWA-9.4 Weak Session IDs(弱会话ID)-Impossible
Impossible Level
查看源码
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
$cookie_value = sha1(mt_rand() . time() . "Impossible");
setcookie("dvwaSession", $cookie_value, time()+3600, "/vulnerabilities/weak_id/", $_SERVER['HTTP_HOST'], true, true);
}
?>
Impossible级别使用随机数+时间戳+固定字符串(”Impossible”)进行 ...阅读全文
抢沙发
May062020
DVWA-9.3 Weak Session IDs(弱会话ID)-High
High Level
查看源码
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
if (!isset ($_SESSION['last_session_id_high'])) {
$_SESSION['last_session_id_high'] = 0;
}
$_SESSION['last_session_id_high']++;
$cookie_value = md5($_SESSION['last_session_id_high']);
setcookie("dvwaSession", $cookie_value, time()+3600, "/vulner...阅读全文
May062020
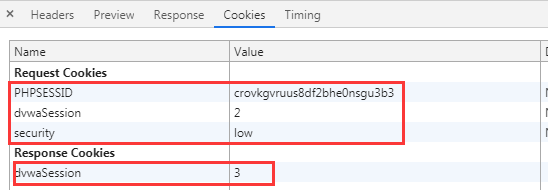
DVWA-9.2 Weak Session IDs(弱会话ID)-Medium
Medium Level
查看代码
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
$cookie_value = time();
setcookie("dvwaSession", $cookie_value);
}
?>
从服务器端的代码来看,将SessionID的值改成了服务器的当前时间,看起来比low的随机了点,但是经过连续的收集后就很容易发现其中的规律。知道时间那我们就可以骗A在某个时间点进行点击,然后你在一个大概...阅读全文
May062020
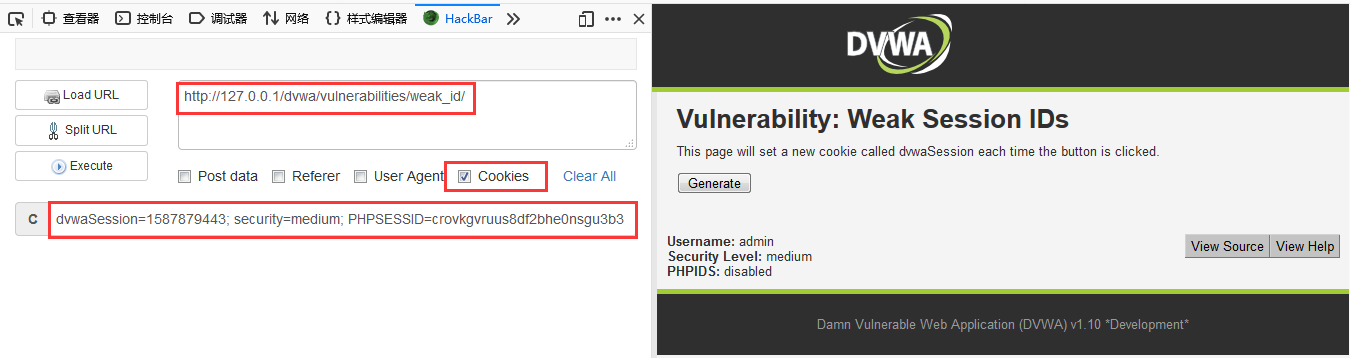
DVWA-9.1 Weak Session IDs(弱会话ID)-Low
Weak Session IDs
当用户登陆后,在服务器端就会创建一个会话(Session),接着访问页面的时候就不用登陆,只需要携带Session去访问。SessionID作为特定用户访问站点所需的唯一内容。如果能够计算或轻易猜到该SessionID,则攻击者将可以轻易获取访问权限,无需登录密码直接进入特定用户界面,进而进行其他操作。
Low Level
查看源码
<?php
$html = "";
if ($_SERVER['REQUEST_METH...阅读全文
May062020
DVWA-8.4 SQL Injection (Blind)(SQL盲注)-Impossible
Impossible Level
查看源码
<?php
if( isset( $_GET[ 'Submit' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
$id = $_GET[ 'id' ];
// Was a number entered?
if(is_numeric( $id )) {
// Check the database
$data = $db->prepare( 'SELECT ...阅读全文
May062020
DVWA-8.3 SQL Injection (Blind)(SQL盲注)-High
High Level
查看源码
<?php
if( isset( $_COOKIE[ 'id' ] ) ) {
// Get input
$id = $_COOKIE[ 'id' ];
// Check database
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $getid ); // Removed 'or die' to suppress mysql errors
// Get results
$num ...阅读全文
May062020
DVWA-8.2 SQL Injection (Blind)(SQL盲注)-Medium
Medium Level
查看代码
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$id = $_POST[ 'id' ];
$id = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $id ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does...阅读全文
May062020
DVWA-8.1 SQL Injection (Blind)(SQL盲注)-Low
SQL Injection(Blind)
SQL Injection(Blind),即SQL盲注,与一般注入的区别在于,一般的注入攻击者可以直接从页面上看到注入语句的执行结果,而盲注时攻击者通常是无法从显示页面上获取执行结果,甚至连注入语句是否执行都无从得知,因此盲注的难度要比一般注入高。目前网络上现存的SQL注入漏洞大多是SQL盲注。
手工盲注思路
手工盲注的过程,就像你与一个机器人聊天,这个机器人知道的...阅读全文
May062020
DVWA-7.4 SQL Injection(SQL注入)-Impossible
Impossible Level
查看源码
<?php
if( isset( $_GET[ 'Submit' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
$id = $_GET[ 'id' ];
// Was a number entered?
if(is_numeric( $id )) {
// Check the database
$data = $db->prepare( 'SELECT ...阅读全文
May062020
DVWA-7.3 SQL Injection(SQL注入)-High
High Level
查看源码
<?php
if( isset( $_SESSION [ 'id' ] ) ) {
// Get input
$id = $_SESSION[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>Something went wrong.</pre>' );
// Get res...阅读全文