May062020
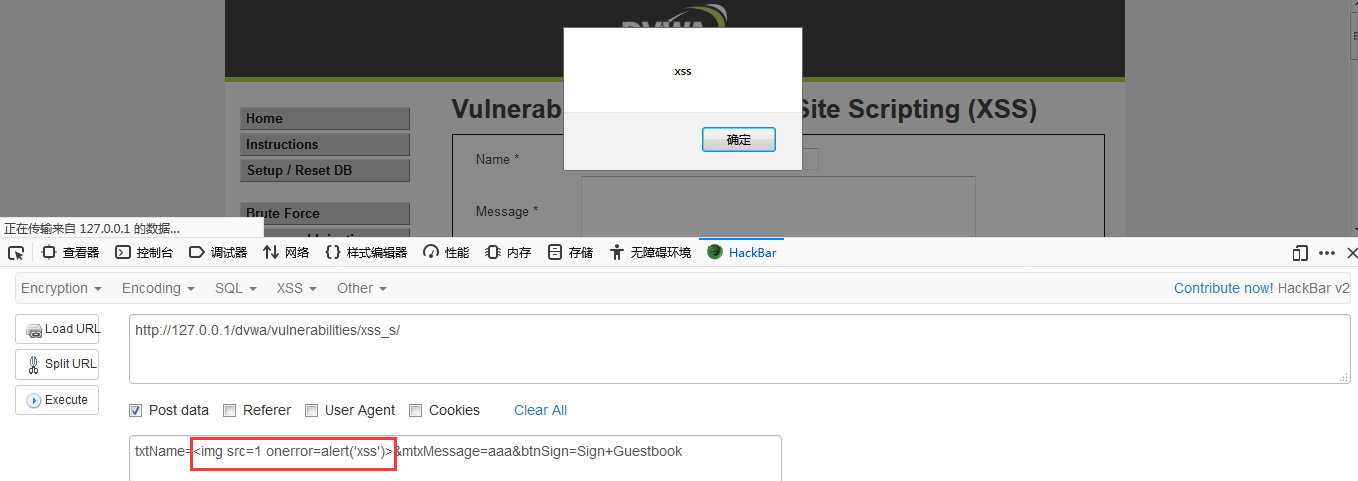
DVWA-12.3 XSS (Stored)(存储型跨站脚本)-High
High Level
查看源码
<?php
if( isset( $_POST[ 'btnSign' ] ) ) {
// Get input
$message = trim( $_POST[ 'mtxMessage' ] );
$name = trim( $_POST[ 'txtName' ] );
// Sanitize message input
$message = strip_tags( addslashes( $message ) );
$message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ...阅读全文
抢沙发
May062020
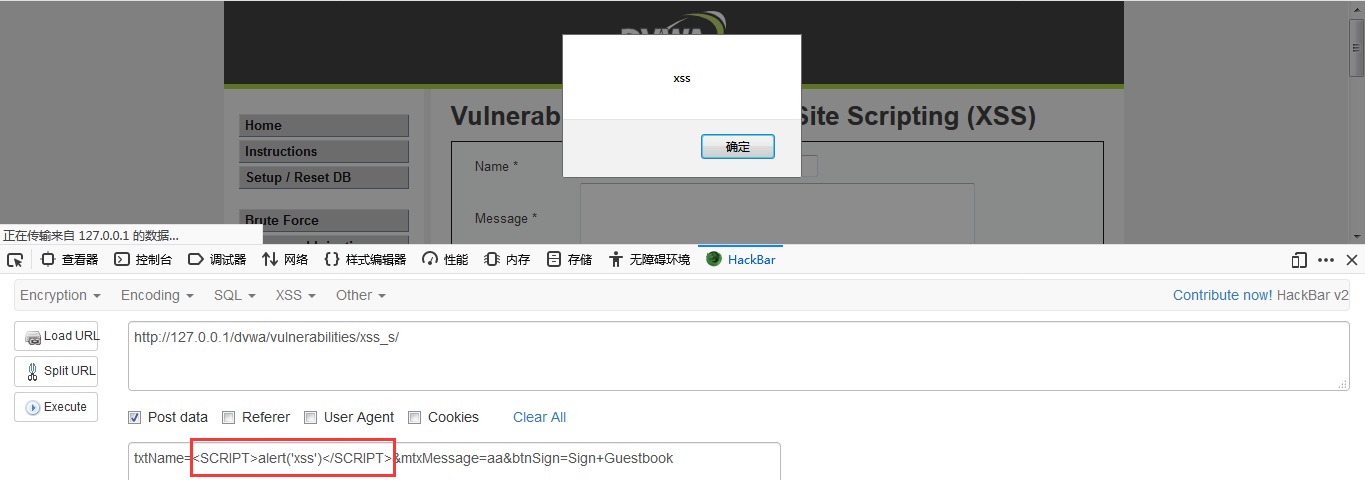
DVWA-12.2 XSS (Stored)(存储型跨站脚本)-Medium
Medium Level
查看代码
<?php
if( isset( $_POST[ 'btnSign' ] ) ) {
// Get input
$message = trim( $_POST[ 'mtxMessage' ] );
$name = trim( $_POST[ 'txtName' ] );
// Sanitize message input
$message = strip_tags( addslashes( $message ) );
$message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])...阅读全文
May062020
DVWA-11.4 XSS (Reflected)(反射型跨站脚本)-Impossible
Impossible Level
查看源码
<?php
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
$name = htmlspecialchars( $_GET[ 'name' ] );
// Feedback for end user
$html ...阅读全文
May062020
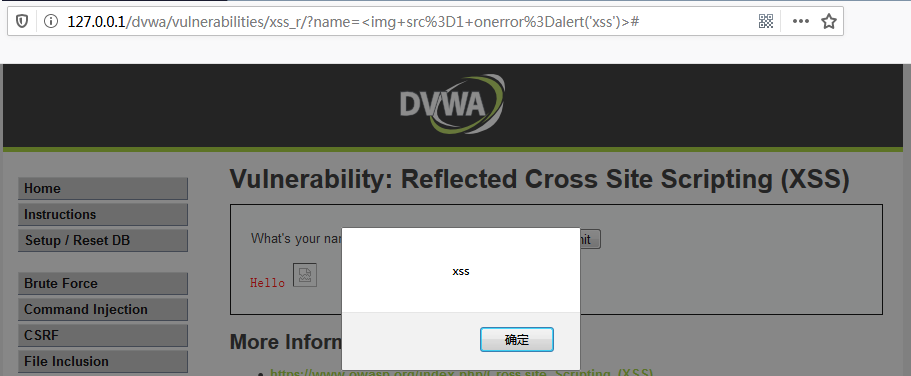
DVWA-11.3 XSS (Reflected)(反射型跨站脚本)-High
High Level
查看源码
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = preg_replace( '/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/i', '', $_GET[ 'name' ] );
// Feedback for end user
$html .= "<pre>Hello ${name}</pre>";
}
?>...阅读全文
May062020
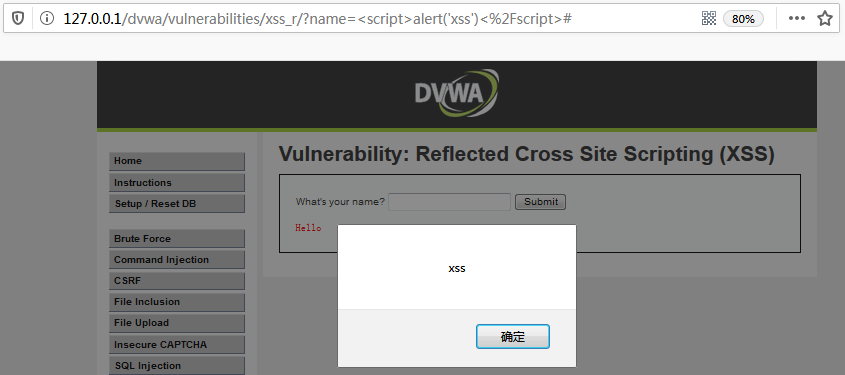
DVWA-11.2 XSS (Reflected)(反射型跨站脚本)-Medium
Medium Level
查看代码
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = str_replace( '<script>', '', $_GET[ 'name' ] );
// Feedback for end user
$html .= "<pre>Hello ${name}</pre>";
}
?>
可以看到,服务器端...阅读全文
May062020
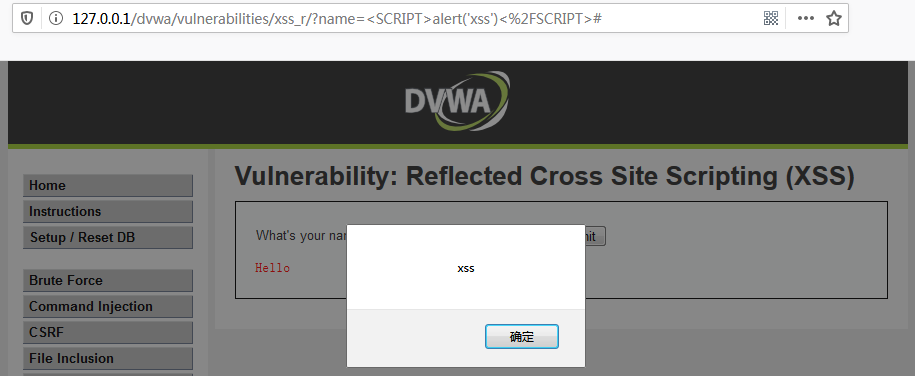
DVWA-11.1 XSS (Reflected)(反射型跨站脚本)-Low
Low Level
查看代码
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Feedback for end user
$html .= '<pre>Hello ' . $_GET[ 'name' ] . '</pre>';
}
?>
array_key_exists() 函数检查某个数组中是否存在指定的键名,如果键名存在则返回 true,如果键名...阅读全文
May062020
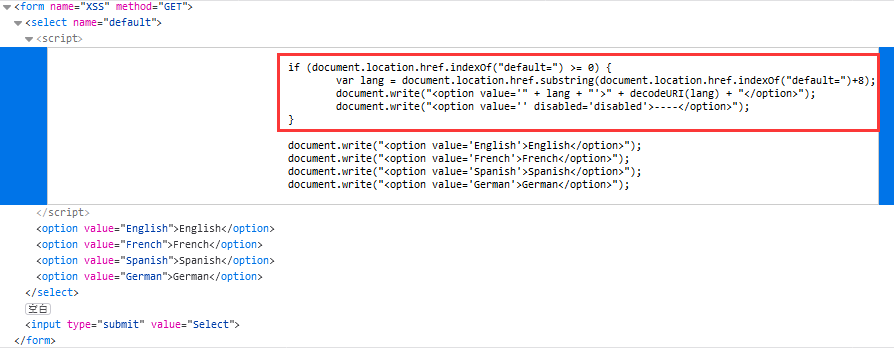
DVWA-10.1 XSS (DOM)(DOM型跨站脚本攻击)-Low
XSS
XSS,全称Cross Site Scripting,即跨站脚本攻击,某种意义上也是一种注入攻击,是指攻击者在页面中注入恶意的脚本代码,当受害者访问该页面时,恶意代码会在其浏览器上执行,需要强调的是,XSS不仅仅限于JavaScript,还包括flash等其它脚本语言。根据恶意代码是否存储在服务器中,XSS可以分为存储型的XSS与反射型的XSS。
DOM型的XSS由于其特殊性,常常被分为第三种,这是一种基于DOM...阅读全文
May062020
DVWA-9.4 Weak Session IDs(弱会话ID)-Impossible
Impossible Level
查看源码
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
$cookie_value = sha1(mt_rand() . time() . "Impossible");
setcookie("dvwaSession", $cookie_value, time()+3600, "/vulnerabilities/weak_id/", $_SERVER['HTTP_HOST'], true, true);
}
?>
Impossible级别使用随机数+时间戳+固定字符串(”Impossible”)进行 ...阅读全文
May062020
DVWA-9.3 Weak Session IDs(弱会话ID)-High
High Level
查看源码
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
if (!isset ($_SESSION['last_session_id_high'])) {
$_SESSION['last_session_id_high'] = 0;
}
$_SESSION['last_session_id_high']++;
$cookie_value = md5($_SESSION['last_session_id_high']);
setcookie("dvwaSession", $cookie_value, time()+3600, "/vulner...阅读全文
May062020
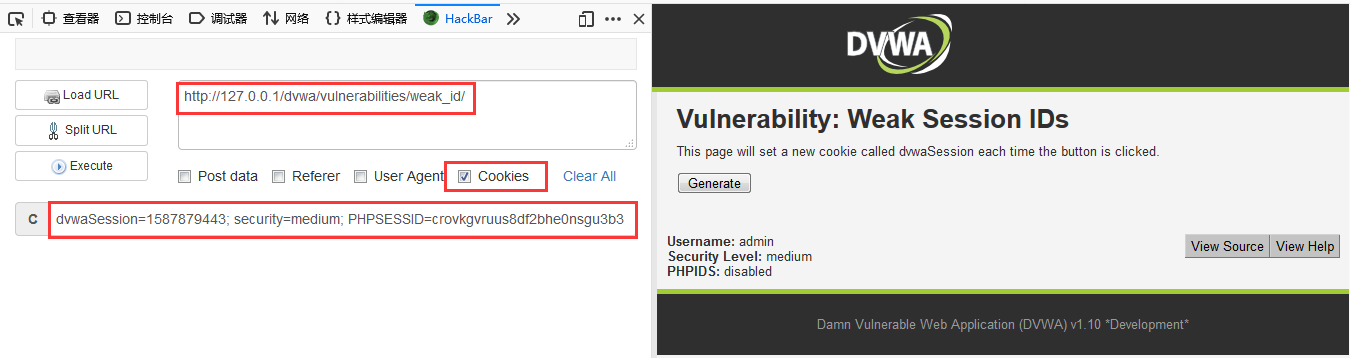
DVWA-9.2 Weak Session IDs(弱会话ID)-Medium
Medium Level
查看代码
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
$cookie_value = time();
setcookie("dvwaSession", $cookie_value);
}
?>
从服务器端的代码来看,将SessionID的值改成了服务器的当前时间,看起来比low的随机了点,但是经过连续的收集后就很容易发现其中的规律。知道时间那我们就可以骗A在某个时间点进行点击,然后你在一个大概...阅读全文